
Sidelink and Its Impact on Lawful Intelligence
Many have used the terms uplink and downlink and they may become more colorful when our video calls drop off. But are “uplink” and “downlink”
Law enforcement agencies (LEAs) all over the world face intensifying personnel shortages. Most are unable to meet recruitment targets or even to compensate for ongoing retirements with new hires.
Ideally, intelligence analysts have the means to structure and correlate data to provide insights that advance their mission. But that vision is often defeated by noisy, siloed data and disjointed toolsets.
With 5G deployments ongoing and 6G some years away, 3GPP Release 18 provides an evolutionary step forward with the first 5G Advanced (5.5G) standard, enhancing performance, efficiency, and flexibility.
Controlling borders is vital to every country’s national interest, from managing immigration to preventing drug smuggling, human trafficking, and terrorism - but physical barriers are no longer enough.
In the coming years, AI is expected to dramatically accelerate the evolution of lawful intelligence, giving law enforcement agencies the ability to efficiently draw insight from data at unprecedented scale.

Many have used the terms uplink and downlink and they may become more colorful when our video calls drop off. But are “uplink” and “downlink”

Having location capabilities in a mobile network was originally an afterthought. The first Global System for Mobile (GSM) network was launched in Finland in 1991

“High-Risk” Providers Recently, we’ve heard a lot about “high-risk” network equipment providers and their potential security vulnerabilities. There is a fear they may be used

Communication Service Providers (CSPs), including those that provide Over-the-Top (OTT) services, are obligated by law, to provide lawful intercept capabilities. This ensures that when law

The last decade has seen an explosion of virtualized deployments for cost saving and flexible deployment scenarios. Virtualization enables Service Providers to quickly deploy 5G

Location information is gathered from connected devices including mobile phones. It is a critical data point which, when used by Law Enforcement Agencies (LEAs), tracks

Communications have shifted from traditional (voice, email and SMS offered by telecom operators) to encrypted, over-the-top (OTT) applications. Which unfortunately leaves law enforcement agencies (LEAs)

As bandwidth increases by up to 100x in the next 24 months, law enforcement agencies (LEAs) may find it difficult to manage the amount of

Gartner publishes Hype Cycle for Threat-Facing Technologies and SS8 is recognized as a sample vendor in the category of Network Traffic Analysis (NTA).
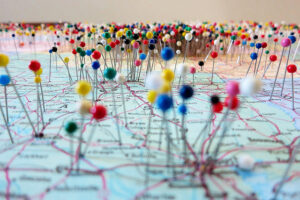
We attended the 2013 Esri International User Conference, held July 8-12 in San Diego, CA, and it was quite an experience. Esri is a dedicated
THE DATA SILO DILEMMA FOR LAW ENFORCEMENT
How to Ingest, Filter and Query 5G Volumes
Webinar Presented by Kevin McTiernan