
Privacy Protections and Lawful Intelligence
Individual privacy and effective law enforcement are both necessary ingredients for democratic civil societies. Those two goals are often at odds with each other, as
In the coming years, AI is expected to dramatically accelerate the evolution of lawful intelligence, giving law enforcement agencies (LEAs) the ability to efficiently draw insight from data at unprecedented
Quantum Computing may enable communications that do not travel across a network in the conventional sense and endanger traditional encryption methods, carrying critical implications for lawful intelligence.
Preventing illicit trafficking is a daunting task for border security agencies. AI-powered Computer Vision and location intelligence enhance security, reduce costs, and close surveillance gaps.
Effective lawful intelligence solutions do more than just ingest and analyze data. They build evidential narratives compelling enough for court that are backed by a fully auditable chain of custody.
Encryption and OTT apps limit the value of lawful eavesdropping tools like wiretaps, but mobile networks offer a powerful engine for new insights: real-time geographical awareness using high-accuracy location.

Individual privacy and effective law enforcement are both necessary ingredients for democratic civil societies. Those two goals are often at odds with each other, as

As criminal activity spreads from the real world to cyberspace and now to virtual worlds, protecting the integrity of digital evidence has become even more

The ability to ingest and analyze an unlimited range of data sources is a key requirement for a modern lawful intelligence practice. The data may

As 5G networks roll out across the world, law enforcement agencies (LEAs) are being forced to reimagine investigation methods related to lawful intelligence. The types

The metadata that surrounds the data payloads for lawful intelligence intercepts has become as important as the payload data itself. Location data, for example, can
As telecom operators plan their rollout of the fifth generation (5G) of network services, two distinct services have emerged, mobile and fixed wireless access (or
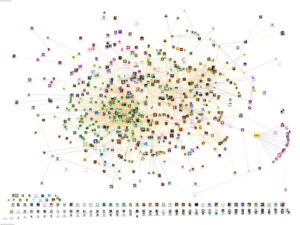
Social Network Analysis (SNA) methods are the subject of this first blog in a series of blogs on analytics techniques, with the discussion focused on

The topic of OSINT (open source intelligence), and specifically social media intelligence, found its way into the defense and military conversation quite frequently at last
THE DATA SILO DILEMMA FOR LAW ENFORCEMENT
How to Ingest, Filter and Query 5G Volumes
Webinar Presented by Kevin McTiernan